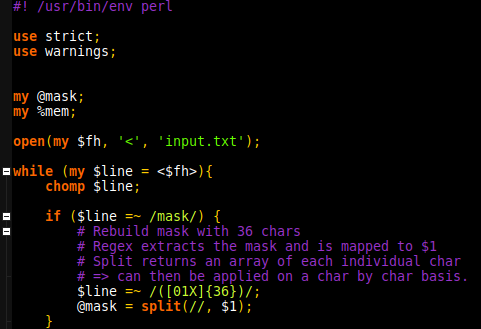
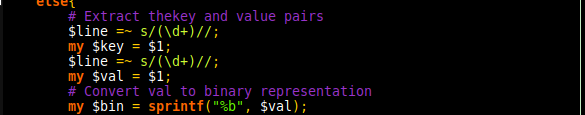
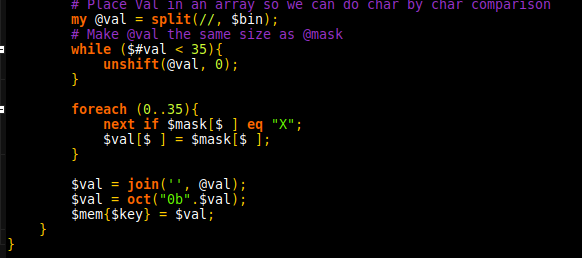
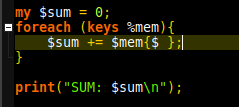
GRIMMCon 0x3 took place on December 30th. The virtual conference hosted 2 tracks (GRIMMCon) with questions being primarily shared in their discord server by hosts to the speakers. As with GRIMMCon 0x1 and 0x2, the conference was held using GoToMeeting which has an interface a fair bit different to Zoom.
Following my talk at Beercon2 and the received feedback, I wanted to provide a different perspective to GDPR. Rather than focus on implementations that may or may not have worked, I wanted to look at how different strategies whcih I’d seen companies take failed to work on a compliance or business level.
The CFP process was fairly simple: fill in a Google form with information about the proposed talk. The form included the option to be paired up with a mentor. Speakers were contacted in early December to confirm their selection, & rookie speakers received an additional email for the speaker-mentor pairing.
I was paired with a mentor local to me (same country) which made finding times to review content far easier than if we had been in opposed timezones. In my case, the content review was more focused on form rather than the actual content given our different specialisations.
Prior to the con I was given links to 2 GoToMeeting events, a green room and the conference. In the Green Room one of the GRIMMCon staff checked the AV settings, and we verified the procedure for sharing the slides. Once all was ready, and a couple minutes before the talk started I joined the main room and repeated the procedure. Perhaps due to user error on my side, when presenting, the video feeds from the hosts disappeared. It was a bit startling to talk at my screen rather than speaking to an audience but overall it went well.
Had the conference been in person I would have done the initial introduction, covering what GDPR is and who it protects and followed on with some wargaming, showing points of failure in various strategies the audience may come up with. Given the nature of the conference I instead presented the strategies in failure from the perspective of a tale, where the characters could always start again with knowledge of their past failures, and ending with the entire company training their teams on procedures & risks.
The strategies used were the following:
1. No strategy
2. Avoid / leave EU market
3. Have a lawyer review contracts with vendors
4. Get an audit
5. Purchase a compliance solution
6. Train the entire company according to their needs.
As was the case in Beercon2, the rookie track was absolutely incredible. The speakers brought some really good insights into their topics which made the talks particularly enjoyable. The rookie talks were recorded and should be appearing on the GRIMM Youtube channel soon.