Everyone receives unwanted messages on a daily basis. Sometimes it’s just marketing, in other cases it’s less benign. In the case of a scam or a phishing attack, the sender wants you to hand over some data (usually financial). Having recently received some unwanted, but benign mail it made sense to show what steps to follow when things seem to be a bit…. odd.
Follow your gut
If a message seems to be telling you to do something urgently, makes you feel under pressure or in any other way uncomfortable, take a step back. Who sent you this email? Were you expecting the email? Does the email have any signs of illegitimacy? By inspecting these you can avoid most of the low hanging fruit that make it past your spam filters. I recently received a (benign) spam message which I’d like to deconstruct.
Who sent you the email?
The first thing to do is verify who sent you the email. Anyone can change the name that appears in the “From” field, email adresses take a little more work to impersonate. If the email is unexpected but from a known source, let them know. Their systems may be compromised and you avoided infecting your own system by verifying. Otherwise, it may come from a very distinctly fake adress.
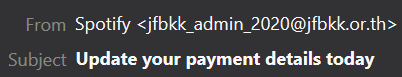
Assuming the sender had managed to spoof the Spotify domain I would still have been able to see that there was an issue, as the recepeint adress had never been linked to Spotify (use a password manager! they help track these things).
Check the links
Usually, links will point to a spoofed domain in an attempt to get PII or CC data. (DHL example here) Will has a great account to follow on Twitter for recent phishing & malware campaigns. In the DHL example, links pointed to the following domains (both are malicious!) sbankrf[.]ru/f4e9f0f6a5/online-gov/wikipedia/ and yoursplace[.]com/invoice.dlh.custumers-pm/ .
Given the initial communication suggested the message came from DHL, it can be seen that neither of the 2 domains is in any way affiliated with DHL. The first URL includes online-gov and wikipedia, neither of which are in any way affiliated with DHL. The second url uses a typo in ‘dlh’ to create the impression of affiliation.
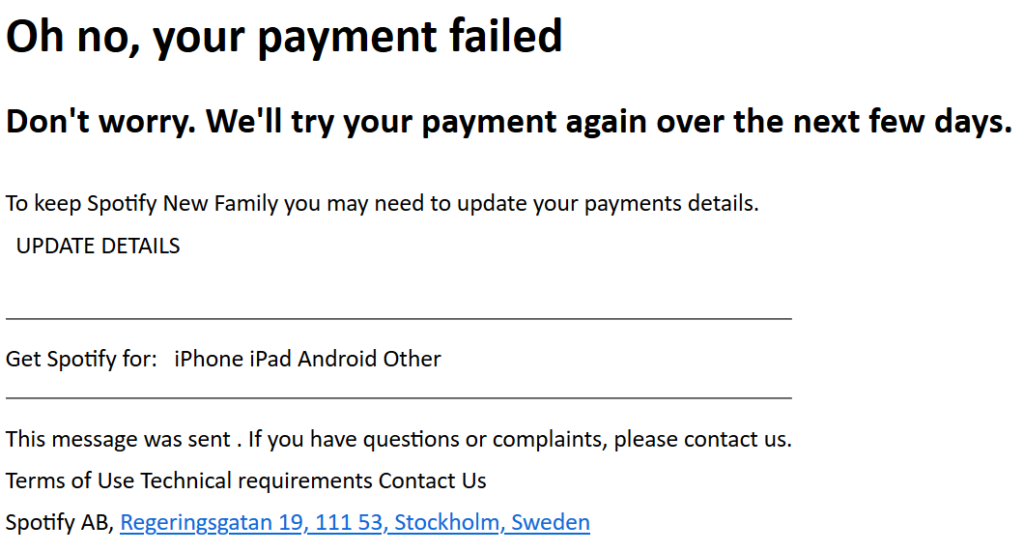
In the case of my Spotify spam… the links pointed to Google maps, at the adress of Spotify HQ in Stockholm, Sweden. As I said, benign message.
Check the Content
Finally, if everything seems legit but you don’t want to bother your friend/colleague/business relation just yet, check the email contents. Many scams contain blatant grammar / spelling errors, with the strategy that those people who click through are more likely to also give up their banking details. Red flags in this case:
Spotify New Family-> At the time of writing, such a subscription did not exist.This message was sent.This sentence is really weird. You would expect “sent by” or “sent from” or event “sent to [email adress]” in order to claim the sender is legit. The sentence as it is, suggests the message was sent by someone with a different primary language, rather than the automatic messages from the company.Terms of Use Technical requirements Contact UsThis final line, just above the Spotify HQ adress, has no links to any of those pages. In a legitimate email those would link to appropriate pages of the website / mail adresses.
What to do after the fact?
Any of the above points should provide enough verification points for the case if a message or sender are legitimate. This leaves 4 possibilities, which can be trimmed down to 2:
- Sender is legitimate => contact sender, verify they intended the message for you.
- If not from sender, follow as though sender is not legitimate.
- Sender is not legitimate => flag it as spam.
In a corporate environment, it’s good to inform your IT/Security departments such that the malicious domains can be blocked and your colleagues better protected.